The procedure to replace SSL certificates has changed in recently released VMware View 5.1 and differs from 5.0 or earlier versions. The main difference is that native Windows certificate store is used. Also it is now necessary to replace or at least to verify self signed certificates otherwise the View infrastructure will not work properly.
Which servers need to replace the certificates? View Connection Managers, Security servers and View Composer. Also vCenter certificate must be replaced or validated.
Although the certificate replacement procedure is described in the manual, the description is very brief and it took me some time to figure it out. I also found an existing blog post which takes different angle here: http://my-virt.alfadir.net/2012/05/generate-view-5-1-certificat/.
The Setup
My lab configuration is following. View Composer is installed together with vCenter. I have two View Connection Managers; one for internal connections and one for external internet connections. I do not use Security server as I use port forwarding to the external View Connection Manager. All servers are in the domain with Enterprise CA which uses self signed certificate.
View Composer Certificate
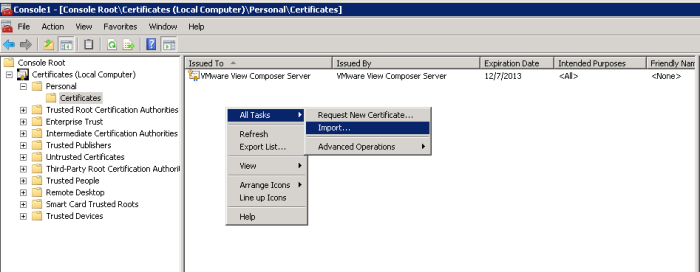
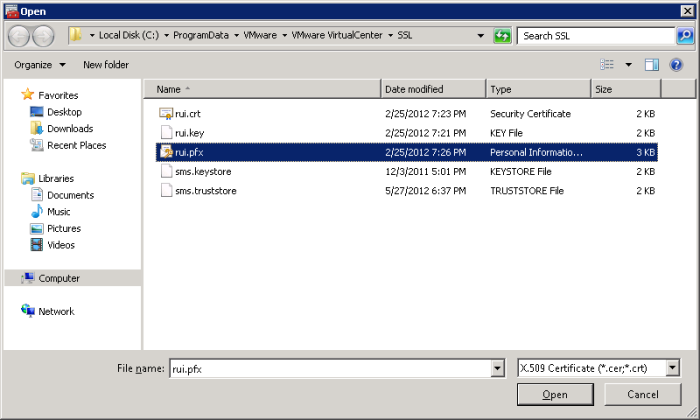
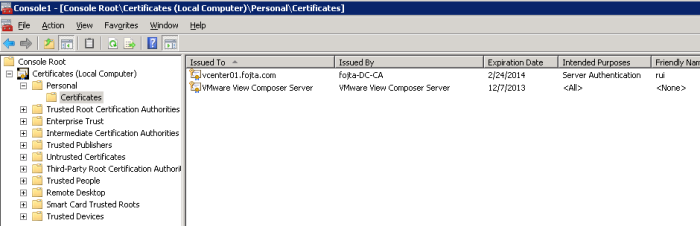
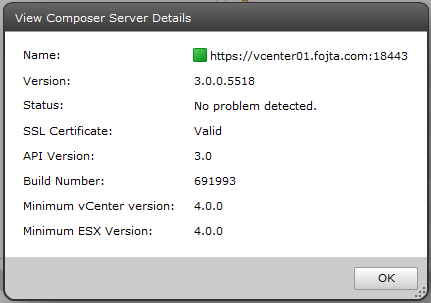
My View Composer server is coexisting with vCenter so I did not need to generate new certificate. I just imported the vCenter certificate from C:\ProgramData\VMware\VMware VirtualCenter\SSL into the local Windows certificate (Personal) store via MMC Certificates Snap-in.
Select the .pfx file which contains both private key and the certificate.
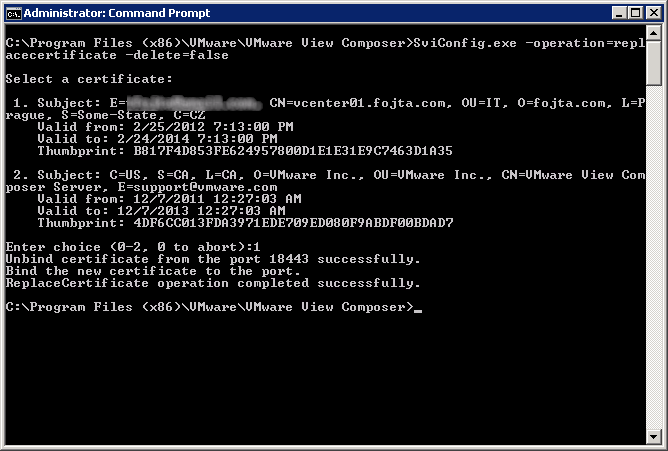
Now we have to stop the View Composer process and run SviConfig command to replace the certificate:
C:\Program Files (x86)\VMware\VMware View Composer>SviConfig.exe -operation=replacecertificate -delete=false
and select the new certificate.
Start the View Composer process again and check the status in the View Administrator.
View Connection Servers
Here we have to generate the certificates. To do this I am again using the Certificates Snap-in. However prior to that I needed to give both of my Connection Server access to Web Server certificate template.
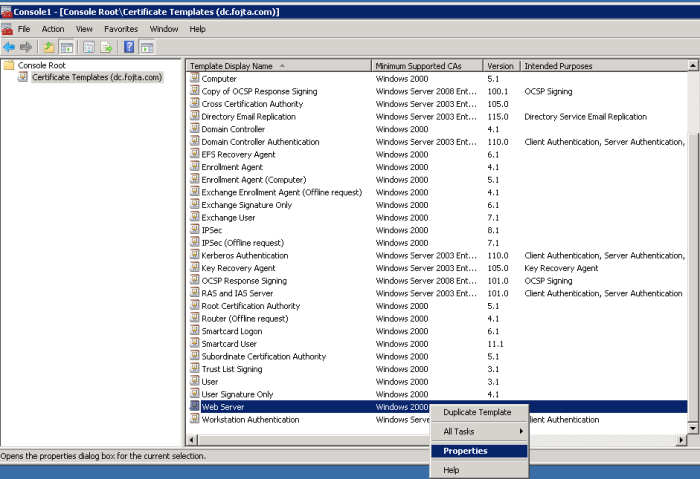
On my CA open the Certificate Templates Management Console Snap-in and open properties of Web Server certificate template.
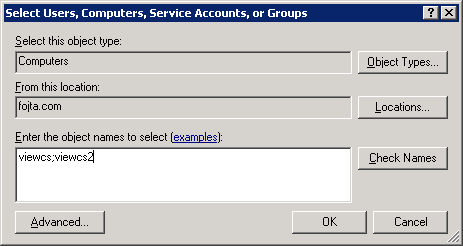
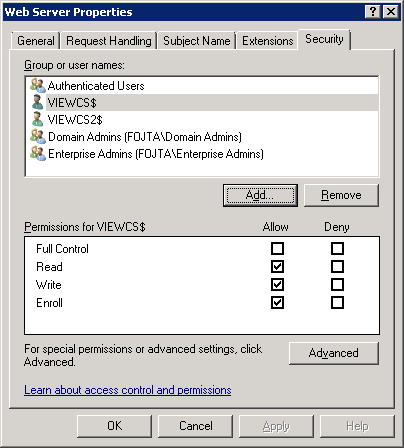
Open the security tab and add both View Connection computers and give them read, write and enroll permissions.
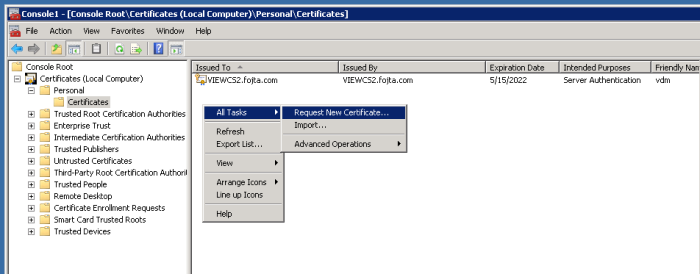
Now we can go to each Connection Server Certificates Snap-in and right click, select All Tasks and Request New Certificate.
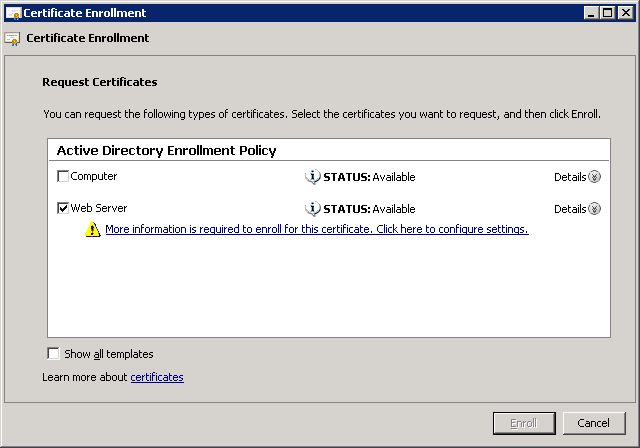
Select Active Directory Enrollment Policy and Web Server certificate template.
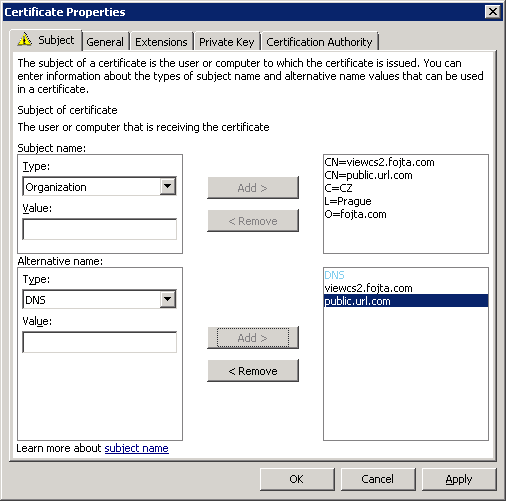
Now we have to add FQDN and additional info to the certificate. Click the More information is required … link.
Type in the Common name (FQDN), Country, Locality, Organization and any other info that will be visible inside the certificate. If your Connection server uses different internal (viewcs2.fojta.com) and public (public.url.com) Fully Qualified Domain Names add both and do the same for the Type: DNS field. The end result should look like this:
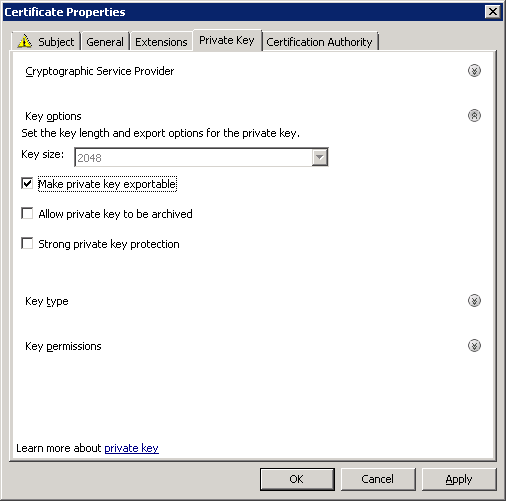
And do not forget to make private key exportable in the Private Key tab / Key options.
Click enroll and finish.
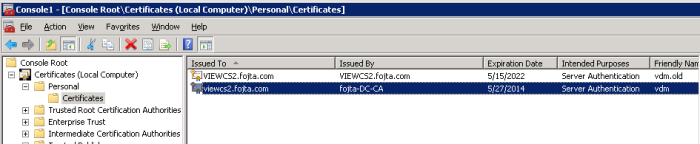
Now we should see the newly created certificate. Last thing we need to do is to change the certificate Friendly Name to vdm. This can be done in the certificate properties. Also we have to rename the original certificate (vdm.old)
Once this is done we can restart the View services.
Repeat for all other View Connection servers and check the result in the View Administrator.
View Clients
As I said at the beginning my CA uses self signed certificate so I have to make sure all the non-domain PCs I use to connect to my View desktops imported the CA Root certificate into the Trusted Root Certification Authorities store.
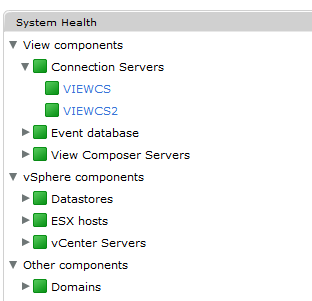
Very helpful. Finally got the green health-status after these instructions. So clear and accurate. Thanks!
Hi Tomas,
I get an error on the first part on “Generate View 5.1 Certificates” when I am want to create the hostname.pfx (page4). I am desperited with the SSL Certs…..
Can I send you my screen with the error?
Thanks a lot!
werner
hello this is a great write up…but my composer and vcenter are on the same server. Yet when I go into my certificates snap in, I only have a SSL cert listed for vcenter not composer. How would I get the composer one in like your screen shot shows?
Hi Tom,
FWIW, I’ve written up a way to generate View 5.1 compatible certificates, if the server is NOT an AD member, so you have to workaround the missing enrollment templates:
http://www.zerouptime.ch/2012/10/manually-generating-view-5-1-ssl-certificates/
Greets, Jonas
Cool guide, thanks
The default PFX password is “testpassword”
My View Composer will not complete the install if I select my CA-issued certificate, but when I choose the self-signed one, it will completely install. Now, if I perform the replacement steps like you have outlined, it does not return a successful certificate replacement. Are there any specific encryption algorithms that VMware favors over others? I forget the error exactly, but it is basically, “failed to replace the certificate. Exit code 4.” At any rate, I searched online for the specific error it returned, and I found nothing that has helped. I’ve even started completely over with the same results. I have already replaced certs on my vCenter and View Connection servers, but View Composer has been the only one complaining.
a certificate for 10.3.1.10 is alreadyu but is not the same as the certificate being presented now, If you choose to install the new certificate fot this connection it will replace the existing trused certificate